How has RDP become a Ransomware Gateway
Ransomware attacks have become a pervasive and costly threat to organizations worldwide. Among the various attack vectors leveraged by cybercriminals, one stands out: Remote Desktop...
Read More
Remote Desktop Protocol (RDP) is the initial attack vector in 50% of ransomware deployments
RDP compromise allows attackers to conduct thorough reconnaissance, identifying valuable assets and vulnerabilities within the network.
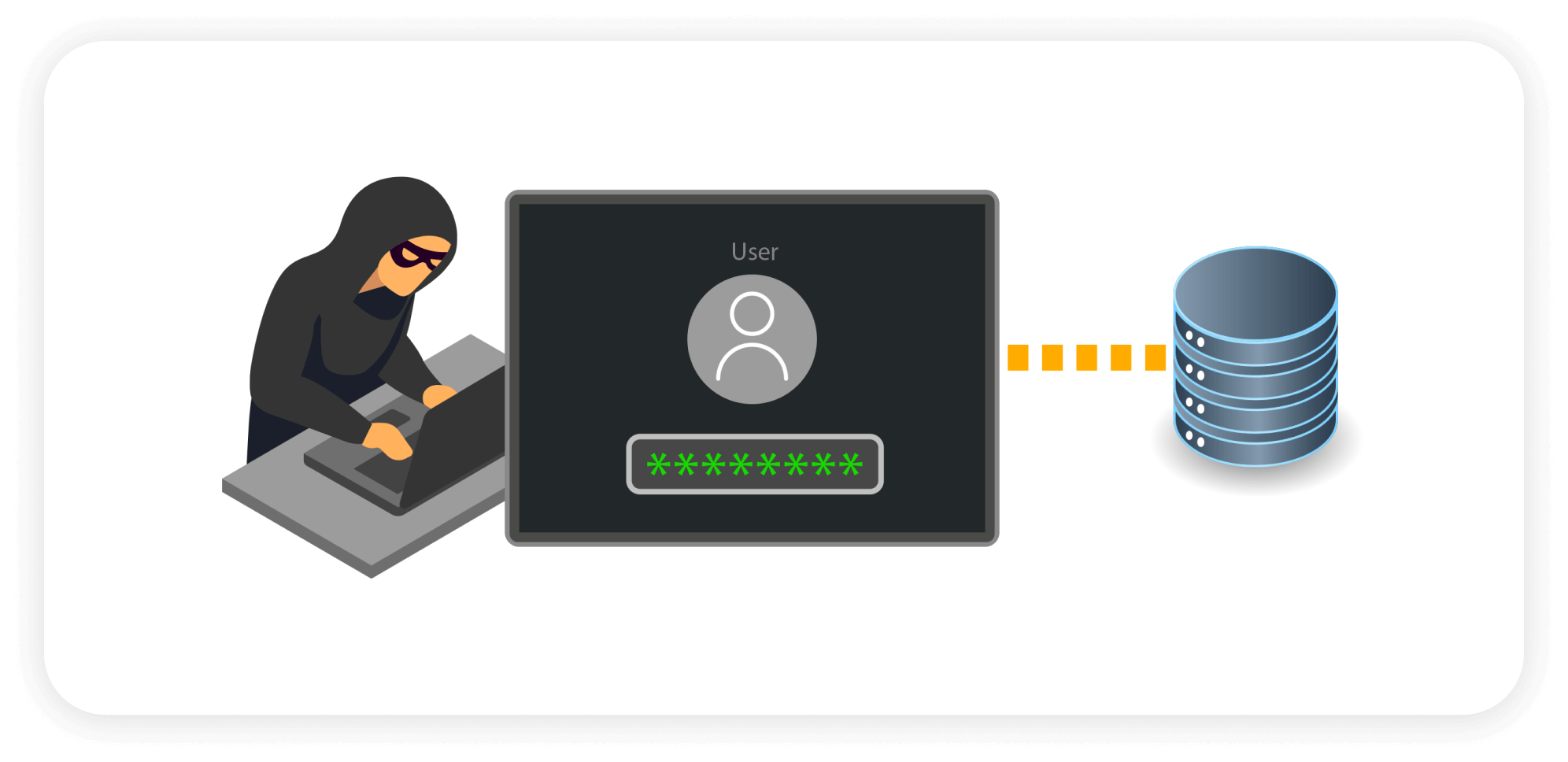
Cybercriminals frequently exploit RDP vulnerabilities to gain unauthorized access, allowing them to move laterally within networks.
Attackers escalate privileges and install ransomware on compromised systems, resulting in data encryption and exfiltration.









Stop The Ransomware Deployment Protocol
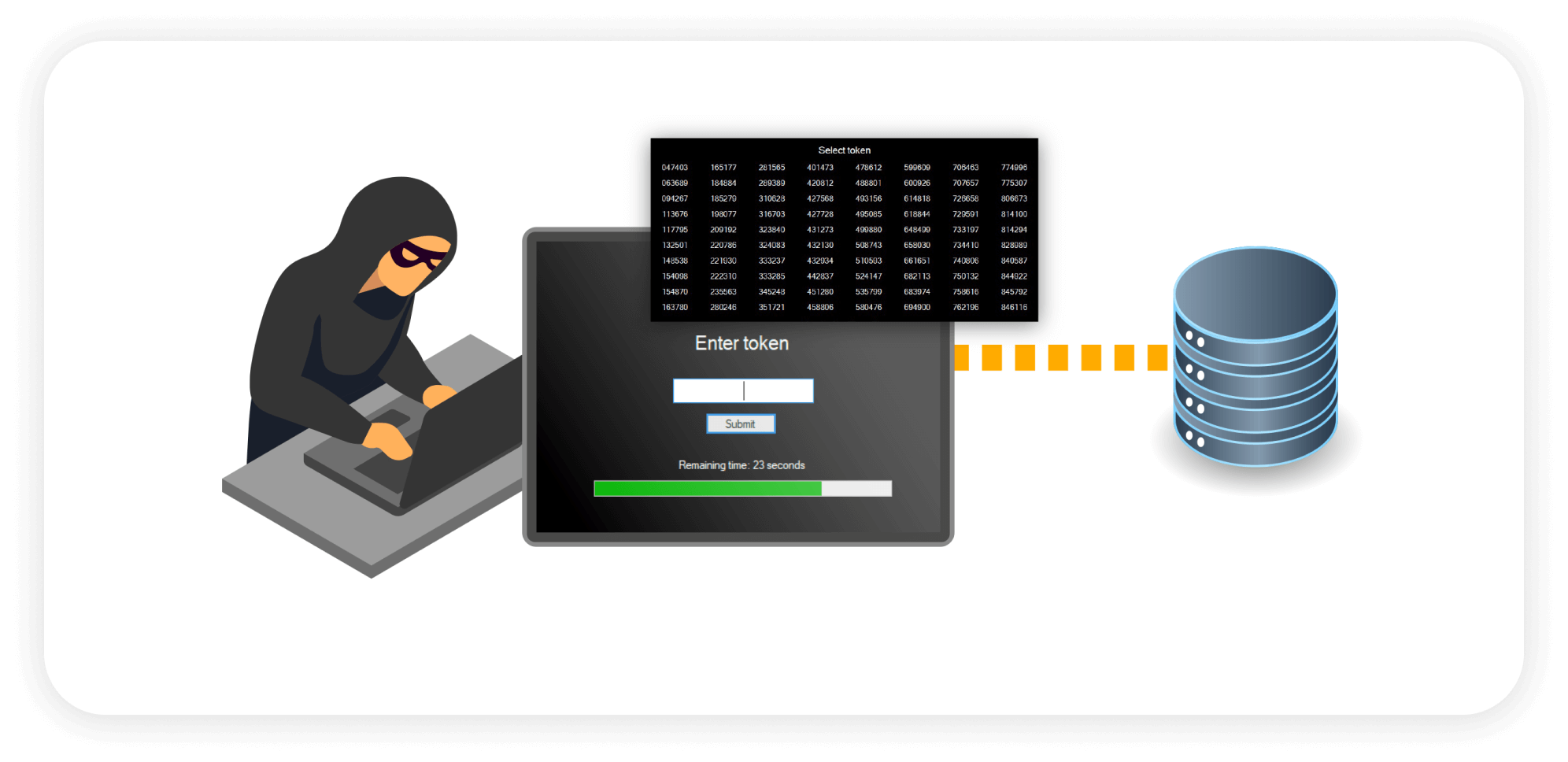
Easy to use, easy to configure MFA with no requirement for a second device.
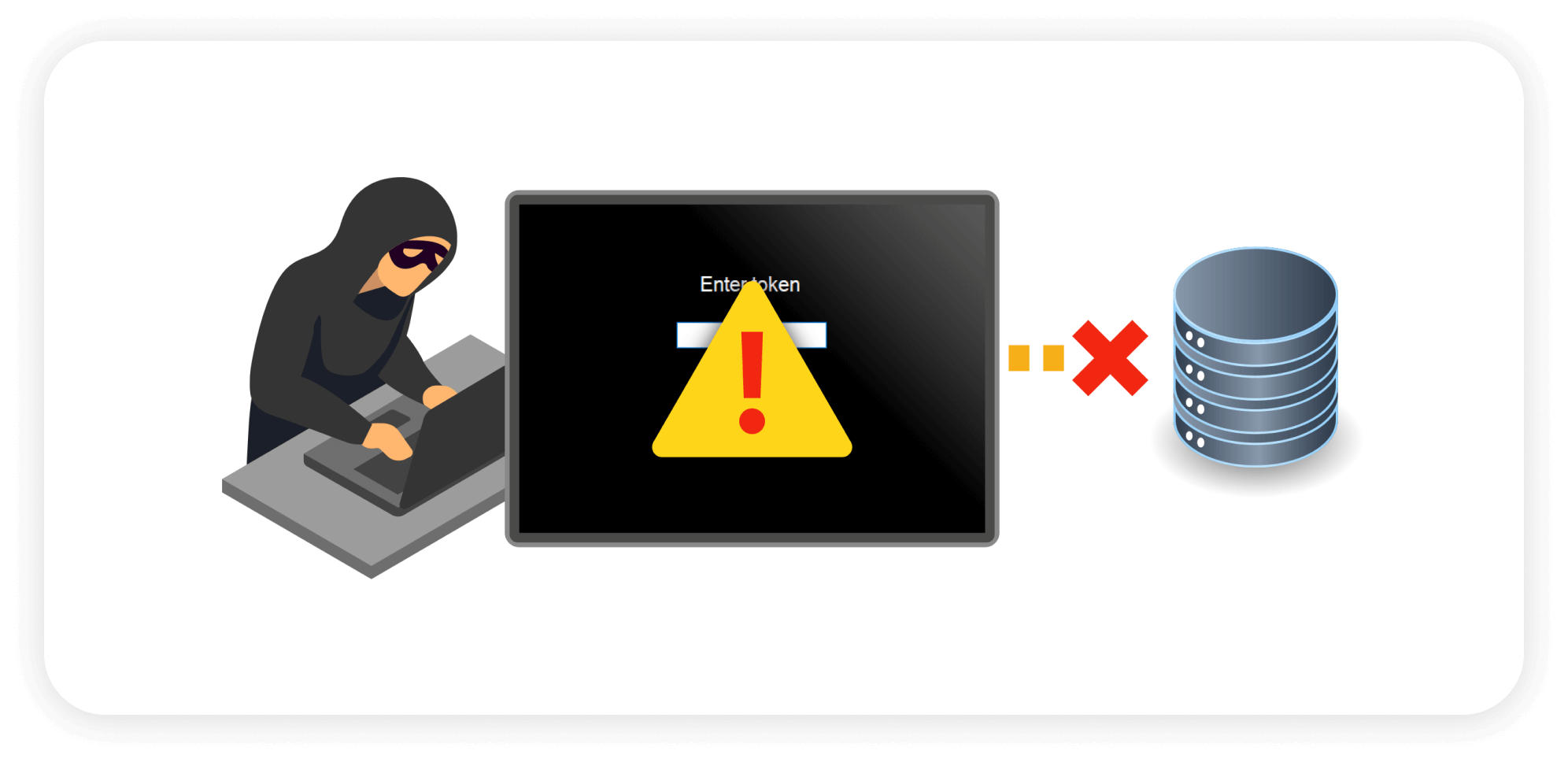
Prevents malware from being installed.
Full forensics on all successful and unsuccessful server login attempts.
cyber insurance policies require MFA on every server login. BullWall ensures compliance.
What if attackers use a different entry point? BullWall contains an active attack.
Ransomware attacks have become a pervasive and costly threat to organizations worldwide. Among the various attack vectors leveraged by cybercriminals, one stands out: Remote Desktop...
Read More

Safeguard Servers From Ransomware
Download

Major European Finance Company $35.8 Million with BullWall
Download