How Ransomware Impacts Educational Institutions
In recent years, ransomware attacks have become a significant threat to organizations of all kinds. Unfortunately, educational institutions are not immune to these attacks. In...
Read MoreMore than 50% of K-12 schools and universities experienced a recent cyber-attack that caused significant disruptions to their IT infrastructure. Educators remain high-level targets due to the complete collection of students' PII data, which can be used for identity theft. While educators understand the issue, they are challenged to improve their security posture with limited budget and staff resources.
This challenge has become more complex with the adoption of remote learning and bring-your-own-device policies, which gives cybercriminals new entry points into school networks. Traditional security solutions are no longer viable in preventing all ransomware variants, and education has the slowest recovery times and the third-highest rate of ransom payment following an attack. Those who paid recovered only 68% of their data, and just 11% received all their encrypted data back, forcing many institutions to rebuild from the ground up and incurring high financial costs.

64%
of universities experienced a cyber attack that caused significant disruption
$73.2M
Cost of downtime accrued by Boston University after an attack
51%
rise in ransomware targeting educational institutions
Think your institution is protected from ransomware? Find out for sure.
In 2022, two-thirds of ransomware attacks against schools were able to successfully exfiltrate data, up from half in 2021. EDR security solutions commonly used in education can’t keep up with ever-evolving cybercriminals and attack vectors. Sooner or later, ransomware will slip through.
When ransomware bypasses preventative solutions, BullWall focuses on minimizing the attack's impact by safeguarding what matters most - school data and student identity. When a ransomware attack begins, BullWall detects the abnormal file activity, stops file encryption within seconds, quarantines the infected user and protects your critical IT infrastructure and data storage – on-premises and in the cloud.
We can’t employ enough people to sit there looking at all of this. We’ve got to automate our response time, our responses, and our monitoring of our system. - Gil Mara, CISO at Torrance Unified School District
The only solution of its kind
BullWall is agentless, lightweight, and easy to get up and running. Entirely automated, the system requires no hands-on monitoring and can be integrated with your other security solutions. BullWall is the first step in strengthening your cybersecurity network and is proven to contain numerous ransomware attempts that target educational institutes.

BullWall is currently protecting 89,000+ school administrators around the world, enabling them to:

In recent years, ransomware attacks have become a significant threat to organizations of all kinds. Unfortunately, educational institutions are not immune to these attacks. In...
Read More
How BullWall Saved Torrance Unified School District from Ransomware
Download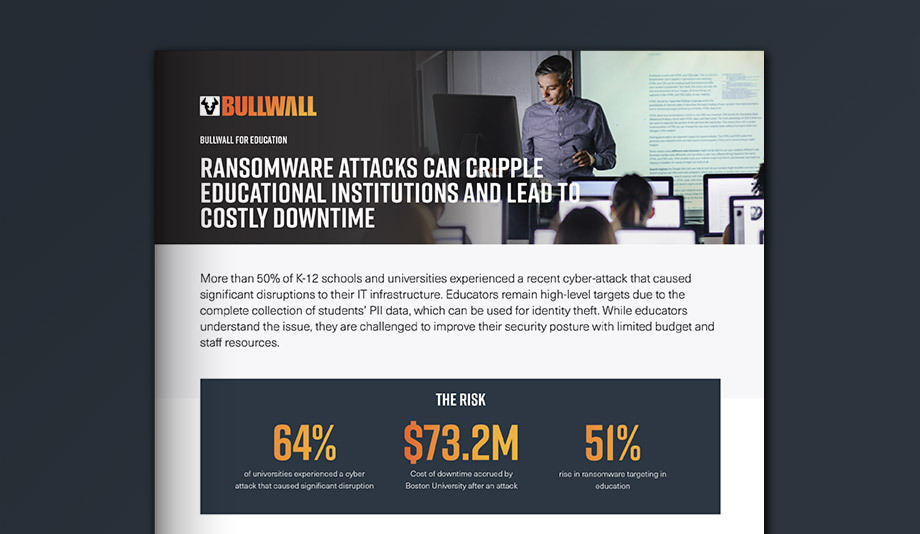
Ransomware attacks can cripple educational institutions and lead to costly downtime
Download